Competitions 2025
NCAE Cyber Games
FEBRUARY 2025
I had the honor of representing DeVry University as part of a 10-member team at the NCAE CyberGames 2025 Regionals for Midwest Region 1. This Department of Homeland Security-sponsored initiative brings together students from NSA-designated Centers of Academic Excellence to engage in cybersecurity competitions that simulate real-world scenarios in defensive security operations.
During the event, I was recognized with the following distinctions:
-
🏅 2025 Competitor Badge
Awarded for successfully competing as part of the official DeVry University team in the Midwest 1 regional event. -
🏆 Most Improved Teammate
Voted by my team as the Most Improved Teammate, acknowledging the noticeable growth in my technical skills, teamwork, and impact throughout the training and competition phases. This recognition reflects my commitment to learning, adapting, and contributing meaningfully to the team’s success.
This competition allowed me to apply and grow my knowledge in areas such as network defense, log analysis, and threat detection, while working collaboratively under time-sensitive, high-pressure conditions. It also strengthened my communication and decision-making skills in a cybersecurity team environment.
Participating in the NCAE CyberGames not only expanded my hands-on experience but also reaffirmed my dedication to continuous improvement in the cybersecurity field.
National Cyber League
April 2025




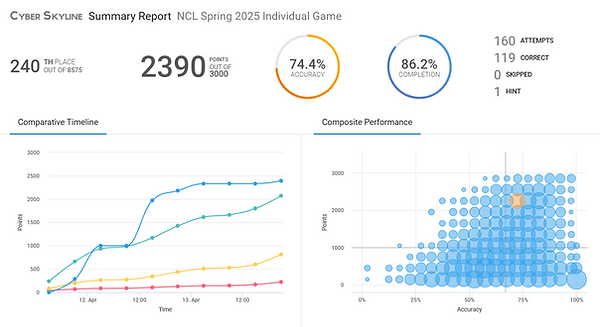
In the Spring 2025 season of the National Cyber League (NCL), I competed in the Individual Game, a solo Capture the Flag (CTF) cybersecurity challenge powered by Cyber Skyline. This performance-based competition is designed to measure real-world technical skills across a wide range of cybersecurity domains, aligned with the NICE Cybersecurity Workforce Framework.
I ranked 240th out of 8,573 participants nationwide, placing in the 98th percentile, with a performance score of 2,390 out of 3,000 points and an accuracy rate of 74.4%. This result represents a significant leap in my growth compared to previous seasons.
My strongest performances were in:
-
Scanning & Reconnaissance – 25th in the nation (100% accuracy & completion)
-
Web Application Exploitation – 99th percentile
-
Enumeration & Exploitation – 99th percentile
-
Password Cracking – 97th percentile (100% accuracy)
-
Network Traffic Analysis – 97th percentile
-
Log Analysis – 93rd percentile
These categories included real-world scenarios such as identifying network vulnerabilities, performing binary and web application exploitation, decrypting and cracking password hashes, and analyzing packet captures and logs for suspicious activity.
To solve the challenges, I utilized and sharpened my skills with tools such as:
-
Kali Linux – for offensive security and scripting
-
Wireshark – for network packet analysis
-
John the Ripper & Hashcat – for cracking hashes with custom wordlists
-
sqlmap & Burp Suite – for web vulnerability testing and automation
-
Binwalk, ImHex, and Ghidra – for reverse engineering and static analysis
-
Volatility 3 – for memory forensics
-
CeWL, Crunch & Hydra – for reconnaissance and brute-force scenarios
This experience not only validated my technical capabilities but also reinforced my ability to work methodically under pressure and prioritize tasks based on time and complexity. I now hold 19 Continuing Education Units (CEUs) recognized by CompTIA due to this performance.
I continue to participate in the NCL as part of my commitment to becoming a well-rounded cybersecurity professional ready for real-world challenges in penetration testing, threat hunting, and security engineering.


Cyber Sentinel Challenge
JUNE 2025
I proudly participated in the Cyber Sentinel Challenge, a national cybersecurity competition hosted by the U.S. Department of Defense (DoD). This highly competitive CTF-style event is designed to identify and strengthen emerging cybersecurity talent through advanced real-world scenarios inspired by DoD cyber defense operations.
As a Participant, I engaged in challenges focused on:
-
Reverse Engineering & Binary Exploitation
-
Cryptography & Password Cracking
-
Web Application Security
-
OSINT & Forensics Investigation
-
Network Traffic Analysis & Anomaly Detection
The competition emphasized teamwork, time management, and the ability to think critically under pressure—skills that are vital in modern cybersecurity operations. I also gained valuable experience using tools such as Kali Linux, Wireshark, Burp Suite, Ghidra, and Volatility, while reinforcing core principles of cyber defense and threat analysis.
Participating in the Cyber Sentinel Challenge was a unique opportunity to measure my skills against national standards and work within a simulated operational environment inspired by the missions of the Department of Defense.
