Competitions 2024
National Cyber League
April 2024
I am an active participant in the National Cyber League (NCL), an esteemed cybersecurity competition designed to provide hands-on experience and bridge the gap between classroom learning and practical skills required in the industry. Powered by Cyber Skyline, NCL offers virtual challenges for high school and college students across the United States.
Through my involvement in the NCL, I have engaged in a variety of tasks, including auditing vulnerable websites, identifying breaches from forensic data, and tackling real-world cybersecurity scenarios. I have demonstrated remarkable progress and achievement despite studying for just four months.
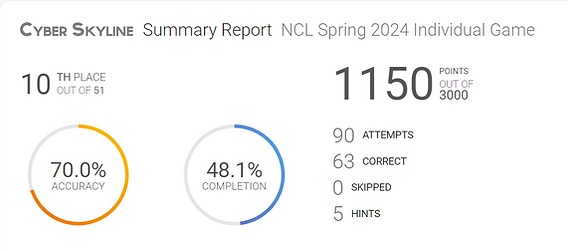
In a competition involving 7370 students, I proudly secured a commendable rank of 1286, placing me in the top 17.5% of participants. Additionally, among my peers at DeVry University, where I am pursuing a Bachelor’s Degree in Information Technology & Networking with a specialization in Security Engineering, I achieved an outstanding rank of 10 out of 51 participants.
Furthermore, our team ranked 262 out of 4212 in the Teams Game, placing us in the top 6.0% of participating teams.
In addition to participating in various challenges, I have also taken on leadership roles within my team. Working in domains such as Password Cracking, Cryptography, Log Analysis, Network Traffic Analysis, and Enumeration & Exploitation, I have contributed to our team's success by leveraging my skills and knowledge in these areas.
I regularly utilize a range of tools to accomplish tasks efficiently. Some of the tools I frequently use include:
-
Kali Linux: A Debian-derived Linux distribution designed for digital forensics and penetration testing.
-
Wireshark: A network protocol analyzer used for network troubleshooting, analysis, software, and communications protocol development, and education.
-
Hashcat and John the Ripper: Password cracking tools used to recover lost passwords through dictionary, brute-force, and hybrid attacks.
-
ImHex: A hex editor designed to quickly and easily manipulate binary files.
-
Volatility 3: An advanced memory forensics framework used to extract digital artifacts from volatile memory (RAM) samples.
-
Binwalk: A firmware analysis tool designed for analyzing, reverse engineering, and extracting firmware images.
-
CeWL: A custom word list generator used to create word lists based on the content of a target's website.
These tools, along with my dedication to continuous learning and skill development, have prepared me for future career opportunities in the dynamic field of cybersecurity.













US Cyber Games
June 2024
I recently took part in Season IV of the US Cyber Open (Beginner’s Game Room)! This event included a series of capture-the-flag challenges that put my cybersecurity skills to the test, covering areas such as cryptography, reverse engineering, PWN, forensics, and web security.
As someone new to cybersecurity, I found the digital forensics challenges especially engaging and enlightening. This experience has been an amazing learning opportunity, and I'm proud to have completed several forensics challenges.
A big thank you to the US Cyber Games for organizing such an incredible event and providing the opportunity to earn this badge. This experience has inspired me to keep honing my skills and deepening my knowledge in cybersecurity.

National Cyber League
November 2024
National Cyber League
- The NCL competition provides students with experience in solving real-world cybersecurity challenges such as identifying hackers from forensic data, pen-testing and auditing vulnerable websites, recovering from ransomware attacks, and more. Participate in the National Cyber League (NCL), a competitive, skills-focused cybersecurity event bridging academic knowledge and real-world industry expertise. Engaged in hands-on cybersecurity tasks, such as identifying vulnerabilities, conducting forensic analysis, and addressing realistic cybersecurity scenarios, demonstrating a strong command of industry-relevant skills.
-
Key Achievements
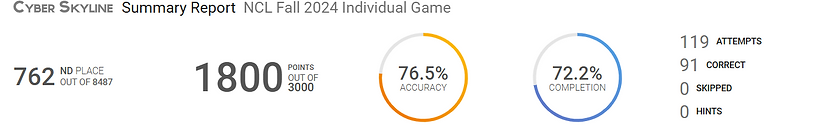
Ranking: Achieved 762 out of 8463 participants, placing in the top 9.0% nationally and ranked 8 out of 51 among peers at DeVry
Team Performance: Leading the team to a rank of 173 out of 4894, placing in the top 3.0% of participating teams
I regularly utilize a range of tools to accomplish tasks efficiently. Some of the tools I frequently use include:
-
Kali Linux: A Debian-derived Linux distribution designed for digital forensics and penetration testing.
-
Wireshark: A network protocol analyzer used for network troubleshooting, analysis, software, and communications protocol development, and education.
-
Hashcat and John the Ripper: Password cracking tools used to recover lost passwords through dictionary, brute-force, and hybrid attacks.
-
ImHex: A hex editor designed to quickly and easily manipulate binary files.
-
Volatility 3: An advanced memory forensics framework used to extract digital artifacts from volatile memory (RAM) samples.
-
Binwalk: A firmware analysis tool designed for analyzing, reverse engineering, and extracting firmware images.
-
CeWL: A custom word list generator used to create word lists based on the content of a target's website.
These tools, along with my dedication to continuous learning and skill development, have prepared me for future career opportunities in the dynamic field of cybersecurity.





Mountain West Cyber Challenge
December 2024
My team—Samantha, Randy, Kevin, and I—represented DeVry University and participated in the Mountain West Cyber Challenge 2024, organized by Deloitte, UCCS, and Rocky Mountain Chapter AFCEA. This was our second competition together, and after hours of intense challenges, we finished in 46th place.
I had the privilege of being the team leader, but leading is easy when you have a team like them. Their dedication, skills, and teamwork made the entire experience enjoyable and productive. Competing on the Hackazon platform tested our technical abilities and our resilience, but it also helped us grow and learn more about cybersecurity.
I am grateful to my teammates for their hard work and commitment, and to the organizers for providing such a valuable experience. We are looking forward to future challenges and opportunities to keep improving.

